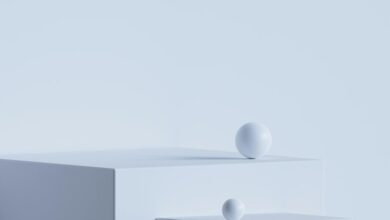
24.0.1.57

The IP address 24.0.1.57 serves as an essential component in network infrastructures. Its role in facilitating communication and optimizing data management cannot be overstated. Understanding the nuances of this address, including its implications for subnetting and security, is critical. As networks evolve, the strategic management of IP addresses like 24.0.1.57 becomes increasingly important. This raises questions about future addressing strategies and their potential impact on network performance and security.
Understanding IP Addresses
Understanding IP addresses is essential for comprehending how devices communicate over networks.
IP address classification divides addresses into categories, facilitating efficient routing and management.
Network address translation (NAT) further enhances this process by allowing multiple devices to share a single public IP address, thus preserving the limited IPv4 space.
This classification and translation are crucial for maintaining connectivity and ensuring user autonomy in digital environments.
The Importance of Subnetting
Subnetting is a fundamental technique in network design that enhances the efficiency and management of IP address spaces. Its advantages include improved security, optimized performance, and efficient routing. By dividing networks into smaller subnets, administrators can allocate resources effectively and minimize broadcast traffic.
| Subnetting Advantages | Efficient Routing | Management Benefits |
|---|---|---|
| Enhanced Security | Reduced Latency | Simplified Maintenance |
| Better Resource Use | Streamlined Traffic | Easier Troubleshooting |
| Improved Performance | Increased Scalability | Network Isolation |
Potential Uses of 24.0.1.57
The IP address 24.0.1.57 can serve multiple purposes within network infrastructures, particularly in scenarios requiring efficient data management and communication.
Its strategic IP address allocation facilitates seamless network management, enabling devices to interact optimally.
Network Security Implications
The examination of network security implications associated with 24.0.1.57 necessitates a thorough understanding of vulnerability assessment techniques, which identify potential weaknesses within the system.
Furthermore, the implementation of effective threat mitigation strategies is crucial for safeguarding against potential attacks.
Access control measures must also be evaluated to ensure that only authorized users can interact with sensitive network resources.
Vulnerability Assessment Techniques
Regularly conducting vulnerability assessments is crucial for maintaining robust network security.
Employing various pen testing methods enables organizations to identify and exploit weaknesses effectively. Coupled with thorough risk analysis, these assessments provide a comprehensive understanding of potential threats.
Threat Mitigation Strategies
Following a thorough vulnerability assessment, organizations must implement effective threat mitigation strategies to address identified risks. These strategies should include robust defense mechanisms tailored to the specific vulnerabilities uncovered during risk assessment. The following table outlines common mitigation techniques and their objectives:
| Mitigation Technique | Objective |
|---|---|
| Firewalls | Block unauthorized access |
| Intrusion Detection | Monitor suspicious activity |
| Encryption | Protect data integrity |
Access Control Measures
Effective access control measures are critical in safeguarding network security, as they define who can access and utilize information resources within an organization.
Key components include:
- Comprehensive access policies
- Robust authentication methods
- Regular audits and compliance checks
- User training and awareness
These elements collaboratively enhance the integrity of the network, ensuring that only authorized users gain access to sensitive data and systems.
Troubleshooting Connectivity Issues
When a user encounters connectivity issues, it is essential to systematically diagnose the problem to restore a functional network environment. Common methods include conducting ping tests to check network reachability and identifying potential DNS issues that may hinder access.
| Step | Action | Outcome |
|---|---|---|
| Conduct Ping | Test connectivity | Response status |
| Check DNS | Verify resolution | Correct address |
| Analyze Results | Identify issues | Troubleshoot further |
The Future of IP Addressing
As the demand for internet connectivity continues to escalate, the evolution of IP addressing is poised to play a crucial role in meeting the needs of an increasingly interconnected world.
Key considerations include:
- Accelerated IPv6 adoption
- Enhanced dynamic addressing techniques
- Improved scalability for IoT devices
- Greater network security measures
These advancements will facilitate seamless communication and empower users with greater freedom in their digital interactions.
Conclusion
In conclusion, the IP address 24.0.1.57 serves as a vital cog in the machinery of modern network infrastructures. Its role in subnetting not only enhances security but also optimizes performance by minimizing unnecessary broadcast traffic. As the digital landscape continues to evolve, the strategic management of such IP addresses will be paramount. Ultimately, without addressing these foundational elements, networks may find themselves lost in the weeds, unable to keep pace with the demands of connectivity.